Getting Started with Cerber Grid and the Cerber Grid Web Interface
- Prerequisite: Set up the Cerber Grid Web Interface and set up Cerber Grid
-
Follow the instructions at Getting Started - Cerber Grid
Follow the instructions at Getting Started - Web Interface
This example uses native bash, so you must be running Linux.
Make sure you start the Controller and at least one Node and that the Node is defined through the web interface so the Controller can see it in the database.
- 2. Create the Job Output Trigger for handling the List of Hosts to Nmap scan
-
In the Web UI click on Job Output Triggers then Create Job Output Trigger.
Name: Nmap Host List Trigger
Type: groovy
script:
if(jobName == 'nmapHostList' && jobStatus != 'failed'){ def nmap = '#HOST# -T5 -O -oX #HOST#_#TIME#.xml' executionGroups.add('linux') jobParameters.put('nmapOptions', nmap) def hosts = jobOutput.split(',') for(i in hosts) { if(i != '') { jobParameters.put('HOST', i) Utils.createNewPluginJob('com.cerbergrid.plugins.nmap.scanner.NmapScanner', 'nmapXmlScan', executionGroups, jobParameters, 'text/plain') } } } - 3. Create the Job Output Trigger for handling the Completed Nmap Scans
-
Create a new Job Output Trigger like in the previous step and use the following values:
Name: Nmap Xml Scan Trigger
Type: groovy
script:
if(jobName == 'nmapXmlScan' && jobStatus != 'failed') { jobParameters.put('input', jobOutput) executionGroups.add('linux') Utils.createNewPluginJob('com.cerbergrid.plugins.nmap.parser.NmapParser', 'nmapXmlParse', executionGroups, jobParameters, 'text/plain'); } - 4. Create the Intial Job which grabs a list of Hosts to scan and Activate the Job
-
Create a new Job in the Web Interface. The Job's name must correspond to the jobName in the first trigger we created and the other way around.
name: nmapHostList
type: bash (native)
Add the following Parameter after you've created the Job:
name: script
value:
nmap -sL 127.0.0.1 | awk 'NF==5 {print $2}' | tr '\n' ','With this script, only one host is going to be returned: our own computer. If you are familar with Nmap you can easily modify this script to scan the entire subnet your computer is on and return all of the hosts.
To clarify what this script does it does an nmap list scan for the given IP range, pull out the hostname from the results and translates all new lines to commas, thus creating a comma separated list of available hosts in the given subnet.
Don't forget to Activate the Job so the controller can see it in the database.
- 5. Watch the Controller and Nodes to view the activity of Jobs.
-
Controller Output:
22:30:27,564 INFO JobDetector:run:51 - Found new job: 37 22:30:27,692 INFO JobSchedulingManager:run:85 - Found new job to assign: [name: nmapHostList, type: bash, id: 37, status: new] 22:30:27,695 INFO RoundRobinMaxJobScheduler:assignJobToNode:65 - Sending job: [name: nmapHostList, type: bash, id: 37, status: new] to node: IpAddress: 127.0.0.1 hostname: localhost port: 7000 status: running 22:30:27,757 INFO IncomingControllerConnection:run:90 - Job: 37 has completed, received Ouput from Node 22:30:37,569 INFO JobDetector:run:51 - Found new job: 41 22:30:38,759 INFO JobSchedulingManager:run:85 - Found new job to assign: [name: nmapXmlScan, type: plugin, id: 41, status: new] 22:30:38,761 INFO RoundRobinMaxJobScheduler:assignJobToNode:65 - Sending job: [name: nmapXmlScan, type: plugin, id: 41, status: new] to node: IpAddress: 127.0.0.1 hostname: localhost port: 7000 status: running 22:30:48,916 INFO IncomingControllerConnection:run:90 - Job: 41 has completed, received Ouput from Node 22:30:57,589 INFO JobDetector:run:51 - Found new job: 42 22:30:57,806 INFO JobSchedulingManager:run:85 - Found new job to assign: [name: nmapXmlParse, type: plugin, id: 42, status: new] 22:30:57,811 INFO RoundRobinMaxJobScheduler:assignJobToNode:65 - Sending job: [name: nmapXmlParse, type: plugin, id: 42, status: new] to node: IpAddress: 127.0.0.1 hostname: localhost port: 7000 status: running 22:30:59,227 INFO IncomingControllerConnection:run:90 - Job: 42 has completed, received Ouput from Node
Node Output:
22:30:27,729 INFO Languages:run:110 - Resovled path to: bash 22:30:27,747 INFO Languages:run:144 - Done, return code: 0 22:30:27,748 INFO IncomingNodeConnection:run:124 - Job 37 completed, returning the error and output to the controller. 22:30:38,776 INFO NmapScanner:run:58 - Executing NmapCommand... 22:30:48,904 INFO NmapScanner:run:88 - NmapScan has completed (Job:41) 22:30:48,910 INFO IncomingNodeConnection:run:124 - Job 41 completed, returning the error and output to the controller. 22:30:59,127 INFO NmapParser:processEndTag:221 - Duplicate Machine found: Machine ID: ipAddress: 127.0.0.1 hostname: null 22:30:59,135 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: F52142A71D1884E4A02546013768536A 22:30:59,142 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 9DBB516CD4DBE85CAEFBE53253BF277C 22:30:59,144 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: EE2A2C9146914C6F0AF43CF3F013CC1C 22:30:59,145 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 526E52BD4F495AA7436D3BC6784D8FE1 22:30:59,147 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: C371ACB3A83F297AEF41DFBCCAA01436 22:30:59,148 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 4DAAAAC22AA3FC20F2D4BA0A402065A2 22:30:59,150 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 32EB3B80029F8547BF7F4CEE3FDEE3BE 22:30:59,151 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 0BD86091B2CD83DFFE9357AA7720405C 22:30:59,153 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: F7133F572EB3D3D1FF92DEFD99E4088F 22:30:59,154 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: CF49F1254F4FA5C6D874A094DAE695E9 22:30:59,155 INFO NmapParser:processEndTag:248 - Duplicate PortInfo found: 00000000000000000000000000000000 22:30:59,159 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 248490FF51AA51BDF29BCDE0A391DE61 22:30:59,160 INFO NmapParser:processEndTag:248 - Duplicate PortInfo found: 00000000000000000000000000000000 22:30:59,162 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 08DEB65002074B0257D74D7F6381FC51 22:30:59,164 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 163EBAC6E1104BB88B4D2D07840447ED 22:30:59,165 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: B67920F5F5B4E43275BAD2936C86C764 22:30:59,166 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 92AA2B398232FF4B0B08BFC596F386BE 22:30:59,167 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 22B5620F033DABA15B0A29B3849CCE19 22:30:59,169 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 900A91BAD5707A64B9098158A9C00ABE 22:30:59,170 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: F1169F61B1A632E25EC9A92996BC6DAC 22:30:59,171 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 07CFDB294104F88F459FF552613CA05F 22:30:59,172 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 2DED9EE693085D1CE386AAC0E459C44F 22:30:59,177 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 41C2DC1EB4A7A1616DE8185D14939A5D 22:30:59,178 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: CBAFCC913A9F9E2ED69EB58D86503DD7 22:30:59,180 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: 1DE262A37F62279C2CED277F717DE79A 22:30:59,182 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: D54E781F52371CEFADD600EC147EBE1C 22:30:59,183 INFO NmapParser:processStartTag:198 - Duplicate PortInfo found: B1679EEB508C37FF86E0A5978CC28A2F 22:30:59,185 INFO NmapParser:processEndTag:267 - Duplicate PortScan found: 8EF85A5FD97A5D2BE8F8AB4C450E2386 22:30:59,201 INFO NmapParser:run:114 - Parsing complete 22:30:59,224 INFO IncomingNodeConnection:run:124 - Job 42 completed, returning the error and output to the controller.
Web UI Output:
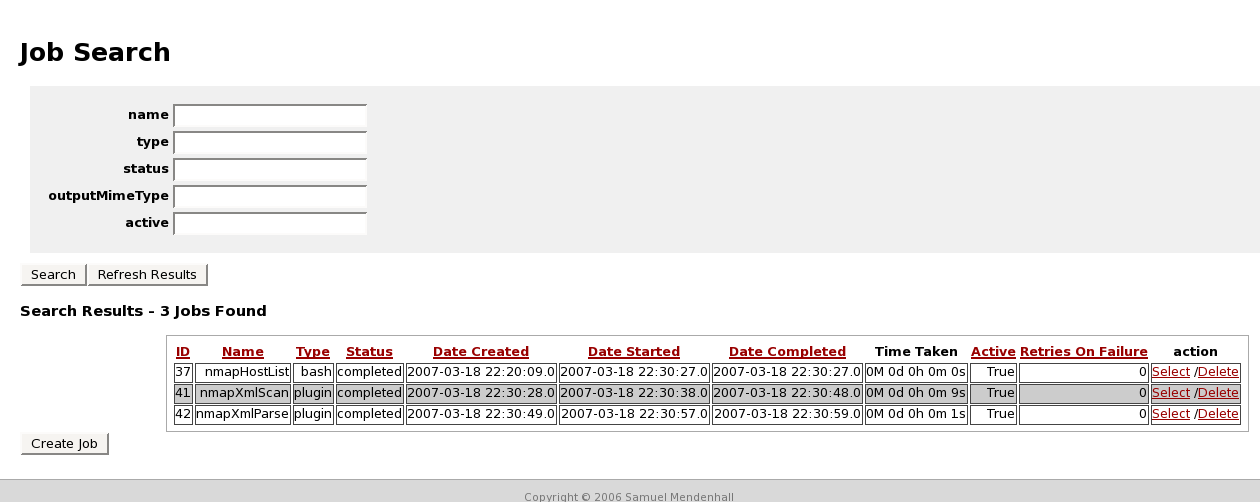
- 6. View the Completed Output of all of the Jobs.
-
nmapHostList Output:
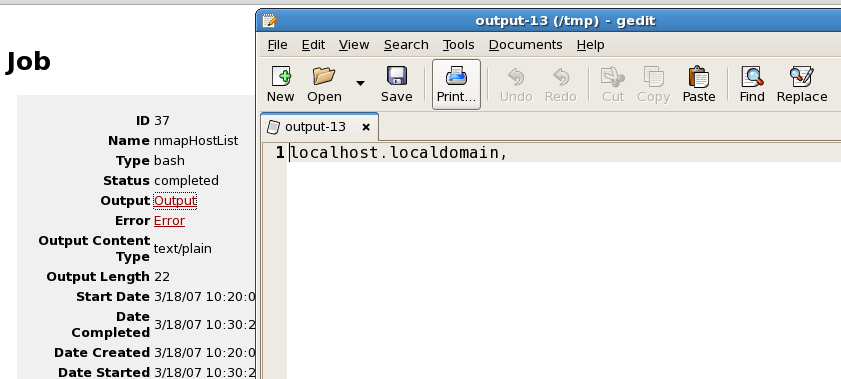
nmapXmlScan Output:

nmapXmlParse Output:
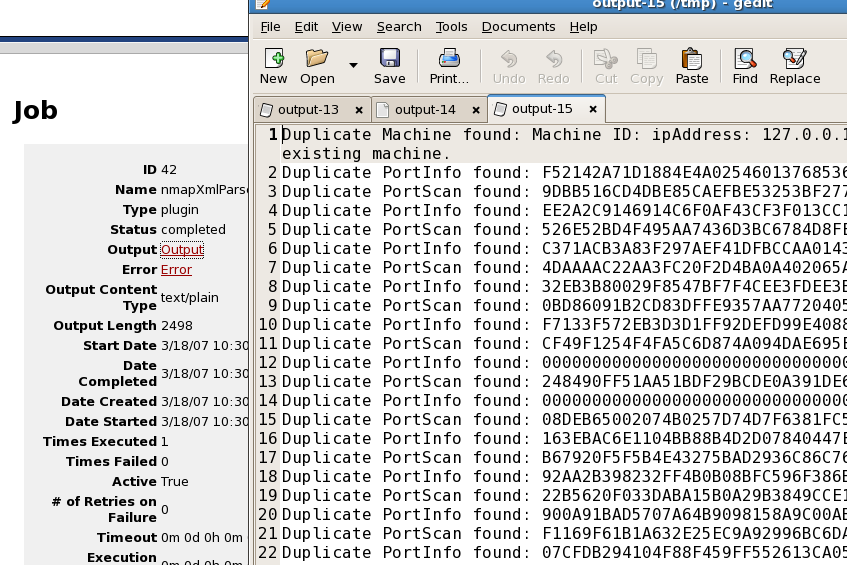
Note that the output shows Duplicate Portscan and Duplicate PortInfo. This is because I reran the scenario twice and the PortScan and PortInfo tables in the database are reused, hence the Duplicate.
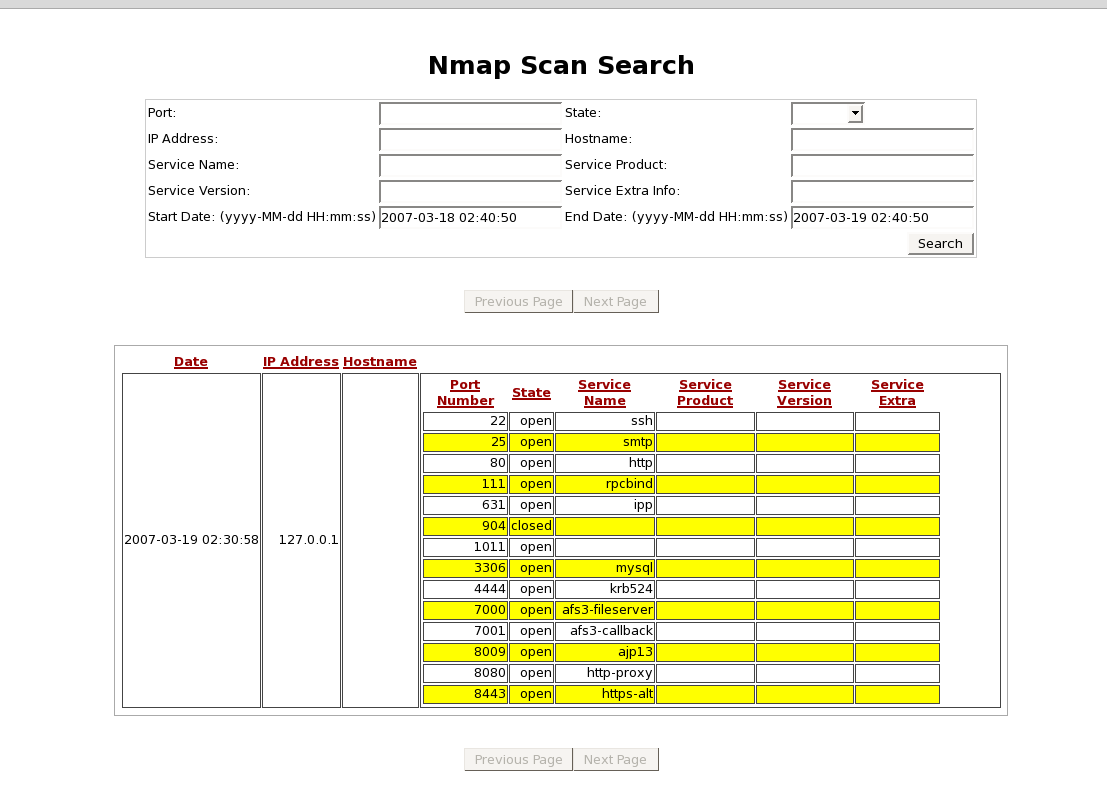
Click on Search under Nmap in the left navigation then change the start date to be less than when you ran the scan and click search and you will see the results of the scan.